ADMINISTRATIVE NOTE:
NEW REQUIREMENTS/PROCEDURES
================================================================
BAA 02-16 PROPOSER INFORMATION PAMPHLET
================================================================
The Defense Advanced Research Projects Agency (DARPA) often selects its research efforts through the Broad Agency Announcement (BAA) process. The BAA will be posted directly to FedBizOpps.gov, the single government point-of-entry (GPE) for Federal government procurement opportunities over $25,000. The following information is for those wishing to respond to the Broad Agency Announcement.
ORGANICALLY ASSURED AND SURVIVABLE INFORMATION SYSTEMS (OASIS) DEMONSTRATION AND VALIDATION (DEM/VAL) PROGRAM, SOL BAA 02-16, DUE: 03/28/03; POC: DR. JAYNARAYAN H. LALA, PROGRAM MANAGER, DARPA/ITO; FAX: (703) 522-7161
BACKGROUND
The Defense Advanced Research Projects Agency (DARPA) has been sponsoring research in the assurance and survivability of information systems for the past few years under the Information Survivability and the Information Assurance and Survivability suite of programs. Many of the research projects have resulted in revolutionary technologies for making DoD’s mission-critical systems and networks highly survivable in the face of large-scale cyber attacks. DARPA is initiating a new two-phase systems program that will integrate and focus these technologies in an exemplar mission-critical system, culminating in a survivable prototype system.
The goals of the OASIS Dem/Val program are to develop survivable system architectures and corresponding assurance arguments. The program is specifically concerned with architectures designed to survive cyber attacks. These include attacks mounted through networks above the physical layer; attacks that attempt to inject malicious software into computers, either when they are being developed or when they are executing; and attempts to exploit accidental software flaws maliciously. This solicitation does not consider physical attacks on the infrastructure, including attempts to destroy computer or communication facilities with kinetic or electromagnetic energy, or the jamming of wireless links. Such attacks are treated in other programs, and effective protective techniques to counter these threats continue to evolve.
This two-phase, two-year systems program will demonstrate a survivable prototype of the Joint Battlespace Infosphere (JBI). A successful demonstration in an operational environment will pave the way for the DoD to infuse cyber survivability throughout its mission-critical systems and networks. It will also accelerate the transition of DARPA-developed cyber defense technologies to the DoD by reducing the risk of employing cutting-edge technologies in DoD’s newer systems and networks that are still on the drawing board.
In the past, survivability has often been an afterthought in the design of information systems. Primary emphasis has been on performance and functionality provided to the user. Non-functional properties such as security, reliability, etc. have been relegated to an appliqué on top of existing architectures, hardware, and software. This program seeks to demonstrate an organic approach to building-in non-functional properties, specifically, survivability in the face of cyber attacks, in mission-critical systems and networks.
Two awards are expected to be made for the system design phase and a down-selection is expected to be made for the system development and demonstration phase. Program duration is 24 months. Awards for the system design phase, 12 months duration, are expected to be up to $5M each and award for the system development phase, 12 months in duration, is expected to be up to $9M.
TECHNOLOGY PROGRAMS
DARPA information technology programs that are deemed directly relevant to the OASIS Dem/Val program are OASIS and Fault Tolerant Networks (FTN). However, it is the responsibility of the proposer to assess the applicability of other DARPA Information Assurance and Survivability programs as well as other government and commercially developed technologies.
ORGANICALLY ASSURED AND SURVIVABLE INFORMATION SYSTEMS (OASIS)
The OASIS Program seeks to provide defense capabilities against sophisticated adversaries to allow sustained operation of mission critical functions in the face of known and future cyber attacks against information systems. The technology development goals are to conceive, design, develop, implement, demonstrate and validate architectures, tools and techniques that would allow fielding of organically survivable systems. The technology products include architectures for building intrusion-tolerant systems from potentially vulnerable components; real-time execution monitors to detect malicious mobile code and prevent damage by and propagation of malicious code; error detection techniques and tolerance triggers; error compensation, error recovery, and error response technologies; and assessment and validation methodologies to evaluate intrusion tolerance mechanisms.
FAULT TOLERANT NETWORKS (FTN)
The FTN Program seeks to ensure the continued availability and graceful degradation of the network infrastructure under partially successful attacks, maximizing the residual capacity available to legitimate users. Technologies are being developed to: (a) ensure the fault-tolerance and secure survivability of critical network services; (b) thwart denial-of-service attacks by constraining an attacker's resource consumption; and (c) trace and contain attacks as close to the source as possible.
OASIS DEM/VAL PROGRAM OBJECTIVES
The principal objectives of this program are to develop an exemplar of a selected Joint Battlespace Infosphere (JBI), from applications down to communications infrastructure, that can operate through a wide class of known and future cyber attacks and to develop system architectures that gracefully degrade system functionality in the face of attacks. The subject system and network will reconfigure dynamically to optimize performance, functionality and survivability as threat conditions warrant.
The cyber-survivability technologies necessary to achieve the OASIS Dem/Val objectives, as previously stated, are being developed under OASIS and FTN programs. Previous DARPA programs in Information Survivability and Information Assurance & Survivability have also produced relevant technologies. The purpose of the OASIS Dem/Val program is to leverage these investments, in combination with commercially available first-generation and second-generation security technologies, to create a pathfinder for the DoD. This program will be one of the major DARPA efforts aimed at accelerating the transition of DARPA-developed cyber defense technologies to DoD operational systems.
PROGRAM SCOPE
The OASIS Dem/Val program will be conducted over approximately 24 months and is divided into two phases. While this solicitation covers both phases, contract award will be made based on the merits of the proposals for Phase 1. Phase 2 will be negotiated with the selected performer after a planned down-select that will be made at the end of Phase 1. Recently, DARPA sponsored a study that produced "Considerations in Developing Survivable Architectures for GIG Systems." This study is intended to be a point of departure for this solicitation. Phase 1 is a 12 month effort and will develop a design and a development plan for the target JBI. A Preliminary Design Review will be conducted late in the 2nd quarter of FY03 and a Critical Design Review will be conducted late in the 4th quarter of FY03. Phase 2 is a 12-month development and test effort. The Phase 2 selection will be based on a competitive evaluation of the design and development plans created in Phase 1. Each design will undergo independent assessment to validate performance predictions and assurance arguments. DARPA reserves the right to select none of the performers at the down-select point.
PROGRAM PHASE DESCRIPTIONS
Preliminary Strawman Architecture Study: A short study was conducted internal to DARPA. Overall goal of the study was to articulate cyber-survivability concepts and principles, discuss current technologies and their vulnerabilities, and show the applicability of DARPA-developed technologies to construct survivable systems and networks. A DoD mission-critical system, Global Command & Control System – Maritime (GCCS-M), was used as a representative operational command and control system. The study also put forward a framework for developing assurance arguments. This study should be considered a point of
departure for the Phase 1 System Design. Distribution of this report is limited to government agencies and their contractors and organizations that qualify for DARPA’s Potential Contractor Program (PCP). Requests for this report should be referred to Dr. Jaynaravan H. Lala (jlala@darpa.mil) at DARPA/ITO.
Phase 1, System Design: DARPA expects to make two awards for this phase. This phase is expected to last about 12 months and provide a funding level of up to $5 million for each award.
Expected Phase 1 products/outputs include an approach to cyber-survivability, threats/attacks/vulnerabilities considered, a strawman survivable architecture for the JBI exemplar system and network, a set of assurance arguments to validate system/network survivability approach, residual vulnerabilities, trade-offs considered in arriving at system and network, architectures, and performance overheads at various survivability operating points (a depiction of the performance, functionality and survivability cone). Other products expected from this phase include a detailed Phase 2 development, implementation, and demonstration plan (including cost and schedule); identification of programmatic risks and an accompanying risk mitigation plan; identification of technology gaps to achieve program objectives and an accompanying risk-reduction plan; and a preliminary assessment and validation plan. The plan should clearly show how the quantitative program goals are going to be achieved.
Phase 2, Development and Demonstration: The Phase 2 development and demonstration effort will be approximately 12 months long and include a funding level of up to $9 million. The performer will be expected to deliver a final Survivable JBI prototype and to demonstrate functional, performance, and cyber-survivability properties of the prototype in the face of a determined Red Team cyber attack. This demonstration will show the impact of cyber survivability features on system and network nominal operations, performance under attack, the capability to operate through attacks, the ability to tolerate malicious mobile code and denial-of-service attacks, and application integrity under attack. Also various operating points (performance, functionality and survivability) will be exercised via dynamic reconfigurations, and the system and networks will demonstrate graceful degradation under attack. Additionally, DARPA, at its discretion, may carry out an independent assessment and validation of the prototype.
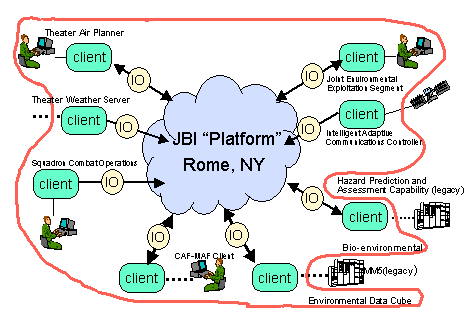
Exemplar Mission-Critical System: The target exemplar military information system of the future is Joint Battlespace Infosphere. Operationally, JBI is a combat information management system. Technically, it is a platform of processes, protocols and common core functions. JBI promotes information interoperability between many individual information systems and acts as an intermediary between these systems. A JBI is a publish/subscribe process involving a set of clients interconnected via a network to a set of core services. The United States Air Force Scientific Advisory Board Report on Building the Joint Battlespace Infosphere (SAB-TR-99-02) of December 17, 1999 may be accessed at http://www.sab.hq.af.mil/archives/reports/index.htm. A password protected information site containing component and client descriptions and high level architectures will be available with the same restrictions as the Preliminary Strawman Architecture Study described earlier, and requests for the URL should be made in the same manner.
The instantiation of a JBI in this program will be the core services and the functional components needed to execute a mission-critical scenario. The scenario starts with an objective that requires an air strike on an enemy target. The near-real time activities include planning an air combat mission based on a set of specified parameters and creating an air tasking order (ATO). The ATO is sent to the squadron for assignment to a ready element. The mission is then executed. At some time between launch but before the objective strike the weather parameters, in this case the winds at the target area, change to such a degree that the predicted collateral damage is unacceptable and a mission modification is necessary. In real-time the ATO is modified and transmitted to the executing element. Throughout the scenario coordination between the mobility command and the combat command is achieved within the JBI. Components and clients included in this instantiation of the JBI are those inside the red line in the figure below.

JBI Instantiation for Dem/Val Program
During this scenario a Red Team conducts a prolonged, determined cyber attack that, if successful, will deny, disrupt, degrade or otherwise harm mission critical functionality of the JBI to the operators. The Dem/Val program will demonstrate the following survivability goals for the exemplar JBI:
attacks within 4 hours with less than 1% false alarm rate.
Unique ideas in regards to intellectual property are solicited; however a minimum of Government-purpose rights will be required to facilitate the ultimate goal of integrating the technologies developed into a JBI.
Proposed research should investigate innovative approaches and techniques that lead to or enable revolutionary advances in the state-of-the-art. However, proposals should be for research that substantially contributes towards the goals stated. Research should result in prototype hardware and/or software demonstrating integrated concepts and approaches. Specifically excluded is research that primarily results in evolutionary improvement to the existing state of practice or focuses on a specific system or solution. Integrated solution sets embodying significant technological advances are expected . Proposals may involve other research groups or industrial cooperation and cost sharing. This BAA shall remain open and proposals received up to one year following this BAA’s release.
SUBMISSION PROCESS
The Defense Advanced Research Projects Agency/Information Technology Office (DARPA/ITO) requires completion of a Broad Agency Announcement (BAA) Cover Sheet Submission for each Proposal, by accessing the URL below:
http://www.dyncorp-is.com/BAA/index.asp?BAAid=02-16
After finalizing the BAA Cover Sheet Submission, the proposer must submit the BAA Confirmation Sheet that will automatically appear on the web page. Each proposer is responsible for printing the BAA Confirmation Sheet and submitting it attached to the "original" and each designated number of copies. The Confirmation Sheet should be the first page of your Proposal. Failure to comply with these submission procedures may result in the submission not being evaluated.
An original and 4 copies of the full proposal, and 2 electronic copies (i.e., 2 separate disks) of the full proposal (in Microsoft Word ’97 for IBM-compatible, PDF, Postscript, or ASCII format on one 3.5-inch floppy disk or one 100 MB Iomega Zip disk). Each disk must be clearly labeled with BAA 02-16, proposer organization, proposal title (short title recommended) and Copy ___ of 2. The full proposal (original and designated number of hard and electronic copies) must be submitted in time to reach DARPA by 4:00 PM (ET) Friday, May 24, 2002, in order to be considered during the initial evaluation phase. However, BAA 02-16, ORGANICALLY ASSURED AND SURVIVABLE INFORMATION SYSTEMS (OASIS) DEMONSTRATION AND VALIDATION (DEM/VAL) PROGRAM will remain open until 4:00 PM (ET) Friday, March 28, 2003. Thus, proposals may be submitted at any time from issuance of this BAA through Friday, March 28, 2003. While the proposals submitted after Friday, May 24, 2002, deadline will be evaluated by the Government, proposers should keep in mind that the likelihood of funding such proposals is less than for those proposals submitted in connection with the initial evaluation and award schedule. DARPA will acknowledge receipt of submissions and assign control numbers that should be used in all further correspondence regarding proposals.
Restrictive notices notwithstanding: Proposals may be handled, for administrative purposes only, by a support contractor. This support contractor is prohibited from competition in DARPA technical research and is bound by appropriate non-disclosure requirements.
EVALUATION AND FUNDING PROCESSES
For evaluation purposes, a proposal is the document described in PROPOSAL FORMAT Section I and Section II (see below). Other supporting or background materials submitted with the proposal will be considered for the reviewer's convenience only and not considered as part of the proposal.
Evaluation of proposals will be accomplished in a two-step process as follows. The first step will be a scientific review of each proposal. The second step will be an oral review. The first step criteria, listed in descending order of relative importance, are as follows:
In step two, the list of winners from the step one evaluation will be asked to make oral presentations. Offerors will be expected to answer a wide range of questions on their proposal, including technical, programmatic, and budgetary matters as well as experience in integrating state-of-the-art information system technologies in large-scale systems.
Evaluation criteria for down-selection to Phase 2 will be communicated to winners soon after the contract award.
Proposals may be reviewed by non-government personnel; however, contractors will not be used to conduct evaluations or analyses of any aspect of a proposal submitted under this BAA, unless one of the three conditions identified in FAR 37.203(d) applies.
The Government reserves the right to select for award all, some, or none of the proposals received. Proposals identified for funding may result in a contract, grant, cooperative agreement, or other transaction depending upon the nature of the work proposed, the required degree of interaction between parties, and other factors. If warranted, portions of resulting awards may be segregated into pre-priced options.
GENERAL INFORMATION
Proposals not meeting the format described in this pamphlet may not be reviewed. Proposals MUST NOT be submitted by fax or e-mail; any so sent will be disregarded. This notice, in conjunction with this pamphlet, BAA 02-16 Proposer Information Pamphlet (PIP) and all references, constitutes the total BAA. No additional information is available, nor will a formal Request for Proposal (RFP) or other solicitation regarding this announcement be issued. Requests for same will be disregarded. All responsible sources capable of satisfying the Government's needs may submit a proposal that shall be considered by DARPA. Historically Black Colleges and Universities (HBCUs) and Minority Institutions (MIs) are encouraged to submit proposals and join others in submitting proposals. However, no portion of this BAA will be set aside for HBCU and MI participation due to the impracticality of reserving discrete or severable areas of this research for exclusive competition among these entities.
NEW REQUIREMENTS/PROCEDURES
: The Award Document for each proposal selected and funded will contain a mandatory requirement for submission of DARPA/ITO Quarterly Status Reports and an Annual Project Summary Report. These reports, described below, will be electronically submitted via the DARPA/ITO Technical – Financial Information Management System (T-FIMS), utilizing the government furnished Uniform Resource Locator (URL) on the World Wide Web (WWW).1) Technical Report
a) Project General Information
b) Technical Approach
- Accomplishments
c) Deliverables
d) Transition Plan
e) Publications
f) Meetings and Presentations
g) Project Plans
h) Near term Objectives
2) Financial Report
3) Project Status / Schedule
1) All Sections of the Status Report
2) QUAD Chart
a) Visual Graphic
b) Impact
c) New Technical Ideas
PROPOSAL FORMAT
Proposals shall include the following sections, each starting on a new page (where a "page" is 8-1/2 by 11 inches with type not smaller than 12 point) and with text on one side only. The submission of other supporting materials along with the proposal is strongly discouraged. Sections I and II of the proposal shall not exceed 40 pages. Maximum page lengths for each section are shown in braces {} below.
Section I. Administrative
{1} Cover Page including: (1) BAA number; (2) Technical topic area; (3) Proposal title; (4) Technical point of contact including: name, telephone number, electronic mail address, fax (if available) and mailing address; (5) Administrative point of contact including: name, telephone number, electronic mail address, fax (if available) and mailing address; (6) Summary of the costs of the proposed research, including total base cost, estimates of base cost in each year of
the effort, estimates of itemized options in each year of the effort, and cost sharing if relevant; and (7) Contractor's type of business, selected from among the following categories: "WOMEN-OWNED LARGE BUSINESS," "OTHER LARGE BUSINESS," "SMALL DISADVANTAGED BUSINESS [Identify ethnic group from among the following: Asian-Indian American, Asian-Pacific American, Black American, Hispanic American, Native American, or Other]," "WOMEN-OWNED SMALL BUSINESS," "OTHER SMALL BUSINESS," "HBCU," "MI," "OTHER EDUCATIONAL," "OTHER NONPROFIT", or "FOREIGN CONCERN/ENTITY."
Section II. Detailed Proposal Information
This section provides the detailed discussion of the proposed work necessary to enable an in-depth review of the specific technical and managerial issues. Specific attention must be given to addressing both risk and payoff of the proposed work that make it desirable to DARPA.
[IMPORTANT NOTE: WITH THE EXCEPTION OF E, C THROUGH H HAVE BEEN REVISED.]
B. {1} A "Proposal Roadmap" which shall address the following nine areas that must be addressed in the proposal. For each area, the roadmap will contain a summary statement (or "sound bite") for that area and identify the page number(s) where the issue is addressed in detail. It is important to make these statements as explicit and informative as possible. The areas are:
1. Main goal of the work (stated in terms of new, operational capabilities for assuring that critical information is available to key users).
2. Tangible benefits to end users (i.e., benefits of the capabilities afforded if the proposed technology is successful).
3. Critical technical barriers (i.e., technical limitations that have, in the past, prevented achieving the proposed results).
4. Main elements of the proposed approach.
5. Specific basis for confidence that the proposed approach will overcome the technical barriers. ("We have a good team and good technology" is not a useful statement.)
6. Nature of expected results (unique/novel/critical capabilities to result from this effort, and form in which they will be defined).
7. The risk if the work is not done.
8. Criteria for evaluating progress and capabilities.
C. {2}Research Objectives:
D. Technical Approach:
E. {3} Statement of Work (SOW) written in plain English, outlining the scope of the effort and citing specific tasks to be performed and specific contractor requirements.
F. Schedule and Milestones:
G. {2}Deliverables Description. List and provide detailed description for each proposed deliverable. Include in this section all proprietary claims to results, prototypes, or systems supporting and/or necessary for the use of the research, results, and/or prototype. If there are no proprietary claims, this should be stated. The offeror must submit a separate list of all technical data or computer software that will be furnished to the Government with other than unlimited rights (see DFARS 227.) Specify receiving organization and expected delivery date for each deliverable.
H. {2}Technology Transition and Technology Transfer Targets and Plans. Discuss plans for technology transition and transfer. Identify specific military and commercial organizations for technology transition or transfer. Specify anticipated dates for transition or transfer.
I. {2} List of key personnel, concise summary of their qualifications, and discussion of proposer’s previous accomplishments and work in this or closely related research areas. Indicate the level of effort to be expended by each person during each contract year and other (current and proposed) major sources of support for them and/or commitments of their efforts. DARPA expects all key personnel associated with a proposal to make substantial time commitment to the proposed activity.
J. {1} Description of the facilities that would be used for the proposed effort. If any portion of the research is predicated upon the use of Government Owned Resources of any type, the offeror shall specifically identify the property or other resource required, the date the property or resource is required, the duration of the requirement, the source from which the resource is required, if known, and the impact on the research if the resource cannot be provided. If no Government Furnished Property is required for conduct of the proposed research, the proposal shall so state.
K. {1} Experimentation and Integration Plans. Offerors shall describe how their results could be integrated with solutions that other contractors are currently developing or are likely to develop. In addition, offerors should identify experiments to test the hypotheses of their approaches and be willing to work with other contractors in order to develop joint experiments in a common testbed environment. Offerors should expect to participate in teams and workshops to provide specific technical background information to DARPA, attend semi-annual Principal Investigator (PI) meetings, and participate in numerous other coordination meetings via teleconference or Video Teleconference (VTC). Funding to support these various group experimentation efforts should be included in technology project bids.
contract and for each contract year. Where the effort consists of multiple portions that
could reasonably be partitioned for purposes of funding, these should be identified as
contract options with separate cost estimates for each. Details of any cost sharing should
also be included.
M. Contractors requiring the purchase of information technology (IT) resources as
Government Furnished Property (GFP) MUST attach to the submitted proposals the
following information:
IMPORTANT NOTE
: IF THE CONTRACTOR DOES NOT COMPLY WITH THE ABOVE STATED REQUIREMENTS, THE PROPOSAL WILL BE REJECTED.Awards made under this BAA may be subject to the provisions of the Federal Acquisition Regulation (FAR) Subpart 9.5, Organizational Conflict of Interest. All affirmations must state which office(s) the offeror supports, and identify the prime contract number. Affirmations should be furnished at the time of proposal submission. All facts relevant to the existence or potential existence of organizational conflicts of interest, as that term is defined in FAR 9.501, must be disclosed in Section II, I. of the proposal, organized by task and year. This disclosure shall include a description of the action the Contractor has taken, or proposes to take, to avoid, neutralize, or mitigate such conflict.
Section III. Additional Information
A bibliography of relevant technical papers and research notes (published and unpublished) that document the technical ideas, upon which the proposal is based, may be included in the proposal submission. Provide one set for the original full proposal and one set for each of the 4 full proposal hard copies. Please note: The materials described in this section, and submitted with the proposal will be considered for the reviewer’s convenience only and not considered as part of the proposal for evaluation purposes.
The administrative addresses for this BAA are:
Fax: 703-522-7161 Addressed to: DARPA/ITO, BAA 02-16
Electronic Mail: baa02-16@darpa.mil
Electronic File Retrieval: http://www.darpa.mil/ito/Solicitations.html
Mail to: DARPA/ITO
ATTN: BAA 02-16
3701 N. Fairfax Drive
Arlington, VA 22203-1714